Information Gathering for a successful Hack
The very first step of a successful hack is Enumeration. Enumeration, alias Reconnaissance is an information gathering process. Its also know as foot printing. As the saying goes ' Information is Power', the more information we can gather, the more there is a chance of a successful attack. Information can be anything about the system and related entities. Methods can be various, that can help us get information about the system or the person or the organisation.
There are several methods of information gathering some of them are discussed as follows.
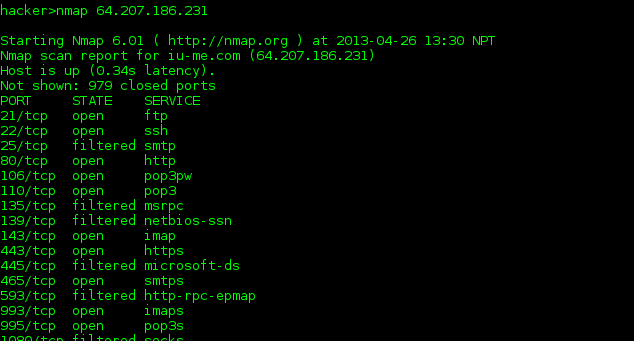
DNS Enumeration is done to find out information about target system/website. This helps us finding out the emails, usernames, ip address, computer names about the system. For this we can use tools like nslookup, whois lookup, dig, traceroute. These will help us find information about the ip address about the system and which will disclose even more information about the system like open ports, operating system, running services, etc.

These days social engineering has become a great tool of information gathering. And of course social networks like Facebook, Foursquare, Twitter, Identica are full of information about our target. Targets website and blogs add additional information for us. Also, search engines like Google,Bing have been great source of information. Dumpster [looking for information in waste reports, papers of the target organization] diving has been great too.
Further more information gathering can be done by active and passive scanning of the target systems. Port scanning is a method of finding out systems that are running. Nmap / Zenmap have been very useful in port scanning.
Sniffing does help know more information about the system. Tools like wireshark, ettercap can capture traffics and manipulate the data. Data being transmitted over wire can be seen using sniffer tools.
We will be discussing on how to use these tools in coming posts. But for now, just know that, the more information about the target the more is the chance of hacking the system. So it has been very important step for hackers to find out as much information as possible about the system to be compromised. All ways 'remember information is power'.

Comments
Post a Comment