How to use nmap - Network Mapper Tool
Nmap [ Network Mapper ] is a network security scanner tool. It is a completely free tool, free as in free beer and free as freedom. That means its free of cost and is open source too. Cool huh? Its extensively used for network discovery and security auditing by System and Network Administrators. It uses the raw packets to find out the characteristics of the system being audited. It helps finding out the operating system running, the running services, firewalls in use, etc. And thus its very useful for System Administrators, Network Administrators and Security Analysts. Its very helpful in gaining information that can be used to compromise a system by hackers. Its available for all of the operating system Linux, Mac, Windows. Its a command line utility tool. However a GUI version is also available, Zenmap.
Now that we have known about Nmap. Lets get it installed in our system. For operating systems viz. Redhat, Fedora, Cent-Os use the command:
And lets get to use Nmap to gather information about a system. Here I'll be testing a TPLink Router using Nmap to demonstrate the usage of it.
Lets check the TPLink Router first. The TPLink Router has an IP 192.168.1.1 for my case.
The basic usage of nmap is to use the command 'nmap ip_address' e.g.
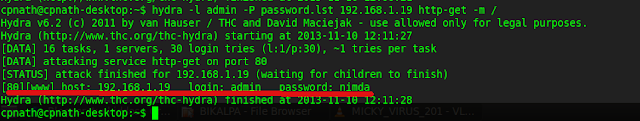
 The above screenshot shows that the TPLink Router has 3 services running, ftp in port 21, telnet in port 23 and http in port 80. To scan a range of IP address we use Nmap as:
The above screenshot shows that the TPLink Router has 3 services running, ftp in port 21, telnet in port 23 and http in port 80. To scan a range of IP address we use Nmap as:
This second image is a screenshot of OS finger printing of the TPLink Router. Since OS Finger Printing requires root privileges we need to use the command with sudo and -O is to tell nmap that we want to do OS Finger Printing. By OS Finger Printing we can see that the Router's MAC Address to be D8:58:4C:BF:59:45 and its running operating system could be Telewell embeded, D-Link Embeded or Linksys embeded. Also it identifies the type of the device to be one among broadband router/webcam/router. That was much information about the device right? Not only this you can also find the version of the operating system, just you need to do is use the -A option with Nmap. In addition it also shows the traceroute information. Below is a screenshot of nmap with -A option.
Nmap uses ping probes to check if the system is up. System can trick to be down by blocking the ping probes. Nmap can overcome this trick. We need to use the option -Pn with Nmap. This makes Nmap think the system to be up and does the port scanning of the system.
By default the scan done by Nmap are for TCP, to scan for UDP we need to use the option -sU with Nmap. Below is a screenshot with -sU option:
We can also scan for a specific port or a range of port for that we use -p option. nmap -p21 192.168.1.1 scans for port 21 to scan for range of port we use nmap -p20-25 192.168.1.1 . This scans the port range 20 to 25.
There are several other options to use with Nmap. To see the help usage of Nmap use the command:
Now that we have known about Nmap. Lets get it installed in our system. For operating systems viz. Redhat, Fedora, Cent-Os use the command:
sudo yum install nmapFor Debian based systems like Debian, Ubuntu, we can use the command:
sudo apt-get install nmapTo check if Nmap is installed in your system use the command:
nmap -VYou should see the Nmap Version that's installed.
And lets get to use Nmap to gather information about a system. Here I'll be testing a TPLink Router using Nmap to demonstrate the usage of it.
Lets check the TPLink Router first. The TPLink Router has an IP 192.168.1.1 for my case.
The basic usage of nmap is to use the command 'nmap ip_address' e.g.

nmap 192.168.1.1-25This scans hosts from IP address 192.168.1.1 to 192.168.1.15. We can also use Nmap to scan a all the hosts in a sub-net by specifying network address/sub-net. e.g.
nmap 192.168.1.0/24The above command will scan hosts in the network 192.168.1.0 with subnet mask 255.255.255.0 i.e. the hosts having IP Address 192.168.1.0 to 192.168.1.255 are scanned.
This second image is a screenshot of OS finger printing of the TPLink Router. Since OS Finger Printing requires root privileges we need to use the command with sudo and -O is to tell nmap that we want to do OS Finger Printing. By OS Finger Printing we can see that the Router's MAC Address to be D8:58:4C:BF:59:45 and its running operating system could be Telewell embeded, D-Link Embeded or Linksys embeded. Also it identifies the type of the device to be one among broadband router/webcam/router. That was much information about the device right? Not only this you can also find the version of the operating system, just you need to do is use the -A option with Nmap. In addition it also shows the traceroute information. Below is a screenshot of nmap with -A option.
Nmap uses ping probes to check if the system is up. System can trick to be down by blocking the ping probes. Nmap can overcome this trick. We need to use the option -Pn with Nmap. This makes Nmap think the system to be up and does the port scanning of the system.
By default the scan done by Nmap are for TCP, to scan for UDP we need to use the option -sU with Nmap. Below is a screenshot with -sU option:
We can also scan for a specific port or a range of port for that we use -p option. nmap -p21 192.168.1.1 scans for port 21 to scan for range of port we use nmap -p20-25 192.168.1.1 . This scans the port range 20 to 25.
There are several other options to use with Nmap. To see the help usage of Nmap use the command:
nmap -hor we can also use:
nmap --help




Comments
Post a Comment